In this article, we will discuss the case of an attack that is becoming very popular: MFA Fatigue and how to reduce the risk of success of this threat with Azure AD.
Defining Mobile Device Management Governance
The following table contains most of the questions and answers that need to be defined to help you define your mobile device management governance.
The following table contains most of the questions and answers that need to be defined to help you define your mobile device management governance.
You can copy and use it, the answers in it are for example.

With these different answers, it is now possible to translate these business requirements into technology capabilities and start building the Intune solution around these specific needs.
Microsoft Intune's Configuration elements
Intune is broken down into several elements to manage the entire fleet of the company's devices.
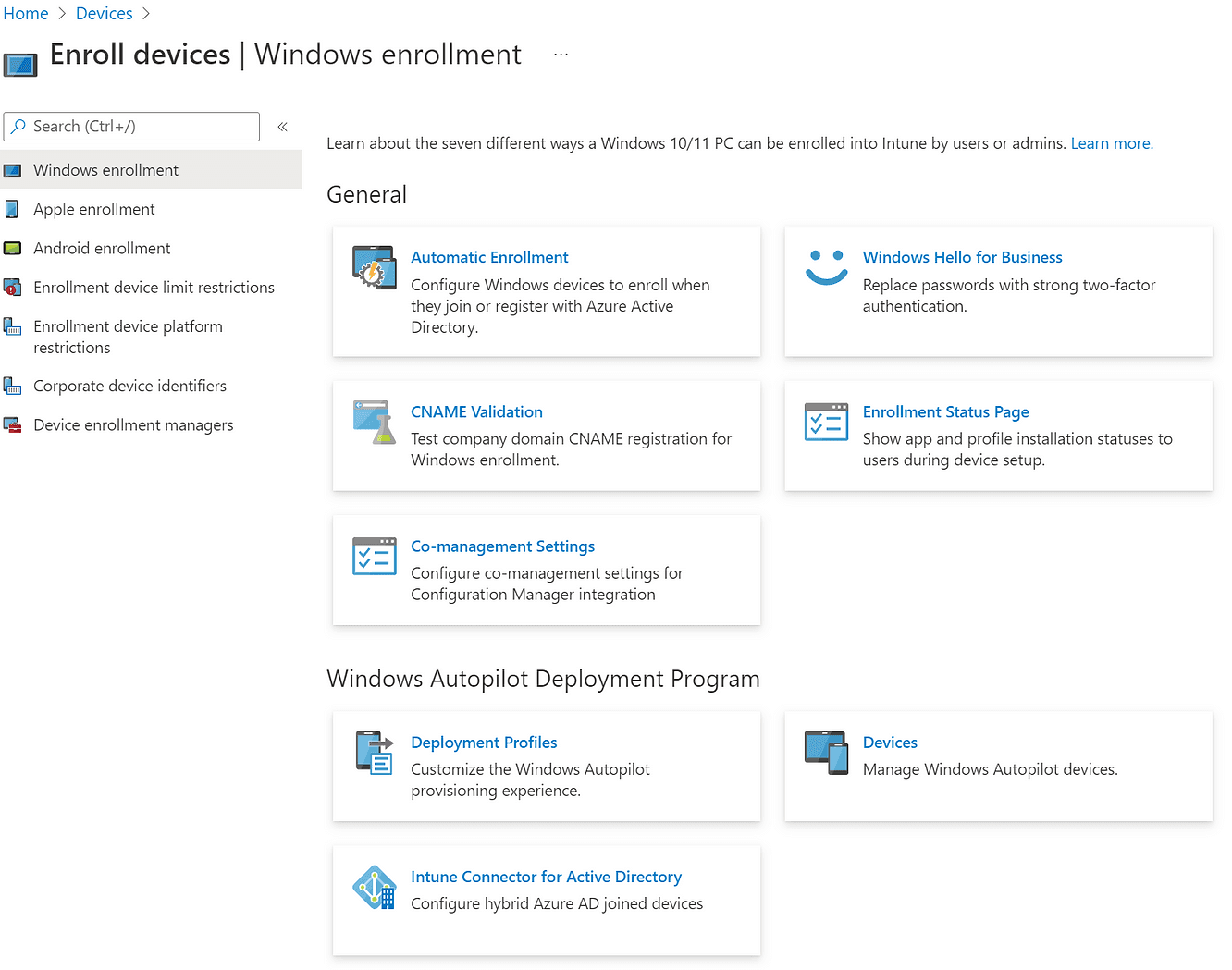
Mobile device enrollment settings
They allow you to manage the different Operating Systems (OS) that can register on Intune, the device enrollment limits per user but also the general connection & configuration settings between Intune and the different OS - Android, Apple, Windows.
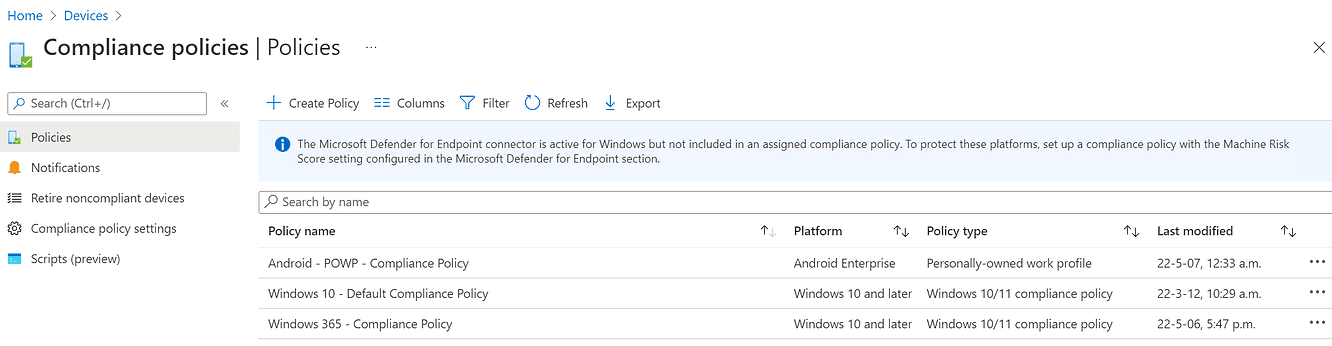
Compliance Policies
These settings govern the rules that devices must comply with in order to register with Intune, according to the rules established by the company.
Example:
The device must not be in Root/Jailbroken mode,
5-character PIN is required to unlock the phone
Ask for a minimum level of security
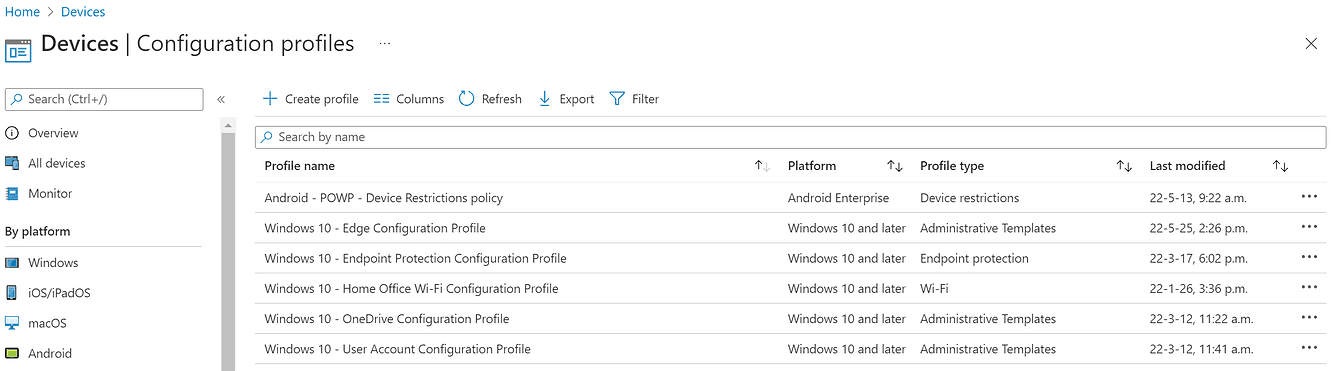
Mobile Configuration profiles
Here we can talk about the mobile device management (or MDM) section.Profiles allow you to push configurations on mobiles.
Example:
Being able to block screenshots,
Request encryption of the device's memory,
Block the use of certain means of biometrics (such as facial recognition)
Application protection policies
This is the mobile app management section in Intune (or Mobile Application Management - MAM).
In this section, it is possible to establish the rules for protecting enterprise-managed applications.
Note:
It's important to understand that these rules only apply to managed apps and data that belongs to the company.
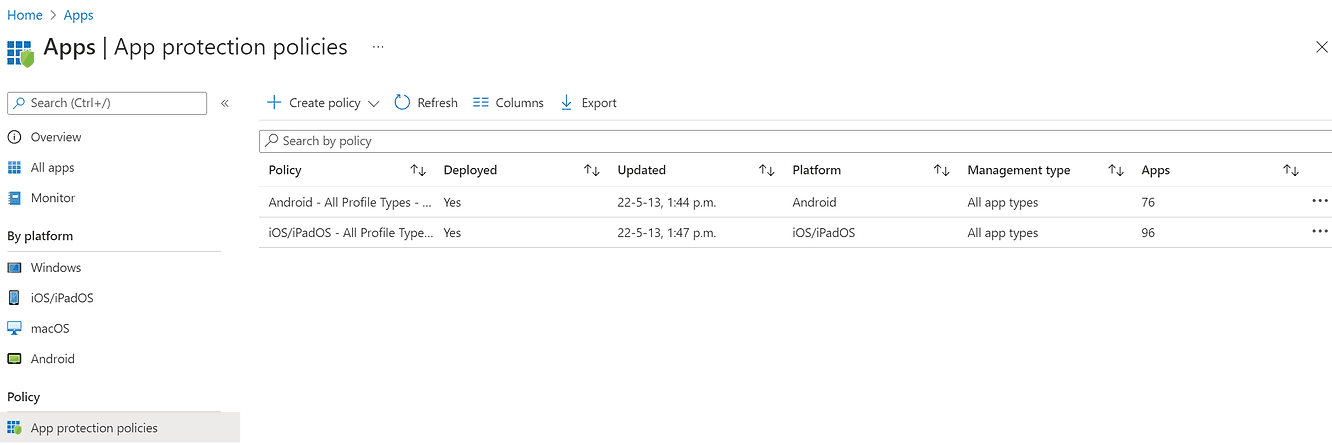
The personal portion of applications and data is in no way affected by these management and security rules.
Similarly, if an employee leaves the company, you can easily and remove the company's apps and data without impacting the employee's personal data and apps.
Application configuration policies
With the same MAM logic, application configuration policies are useful when you want to configure in a personalized way, the different applications managed by the company.
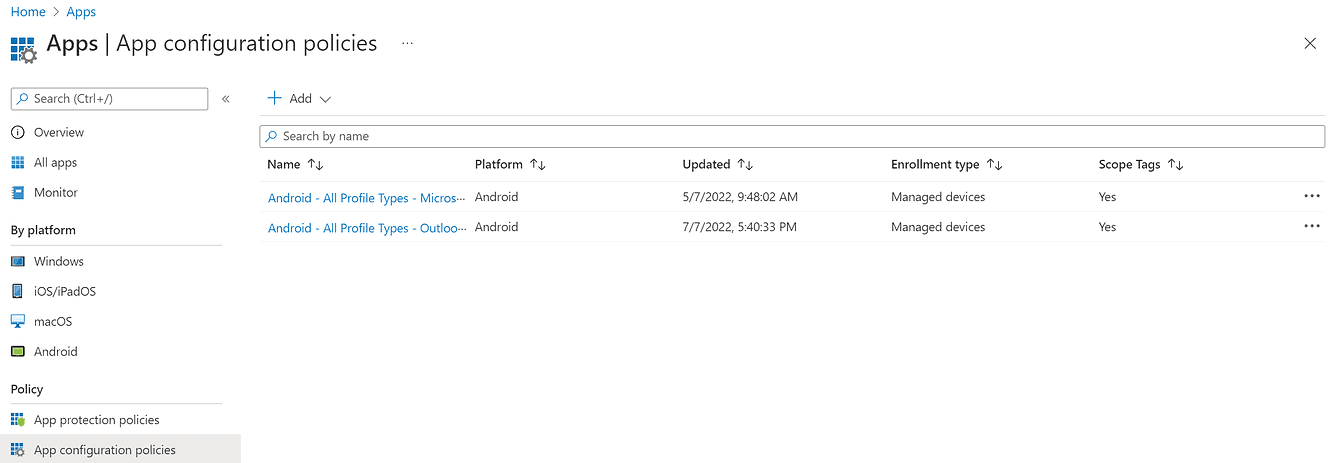
Outlook application can be customized to:
Automatically configure the company account
Use of the default signature
Display of an alert if an external recipient is added to an email
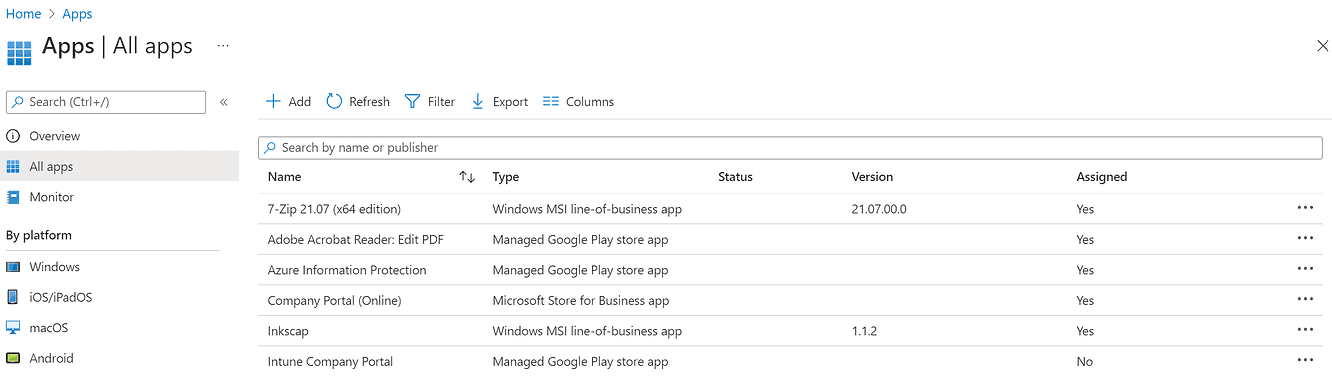
Application deployment
To close on the MAM portion, Intune also allows you to deploy applications on Android, iOS/iPadOS, MacOS and Windows.
Each Operating System has its particularities. It's also possible to install or even uninstall apps according to user groups (or personas) centrally through the Intune app management console.
In the next article, we will explore each of the configuration items in order to meet the different business needs that have been established.